In today’s hybrid work environment, protecting your organization’s data and access points has never been more important. Conditional Access policies in Microsoft Intune (via Microsoft Entra ID) give businesses a powerful way to secure access to cloud apps, devices, and users — but setting them up correctly can be complex.
That’s where partnering with a trusted MSP in Canada like System Support Canada can make a world of difference. With over 15 years of experience providing full-stack IT support in Toronto, our team helps small and medium-sized businesses (SMBs) deploy advanced security and access management policies confidently — without disrupting day-to-day operations.
In this post, we’ll walk you through how to create a Conditional Access policy in Microsoft Intune, and highlight why expert guidance from a 24/7 IT support team matters for long-term security and compliance.
What Is a Conditional Access Policy?
Conditional Access is a feature in Microsoft Entra that helps organizations control access to apps and data based on conditions such as user risk, device compliance, or location. It’s a cornerstone of modern cybersecurity — combining identity protection with real-time access intelligence.
For example, you can allow access only from trusted devices, require multi-factor authentication (MFA) for high-risk users, or block sign-ins from unfamiliar locations. These controls protect your cloud environment from unauthorized access and potential breaches.
Step-by-Step: Creating a Conditional Access Policy in Microsoft Intune
Follow these steps to set up your first Conditional Access policy:
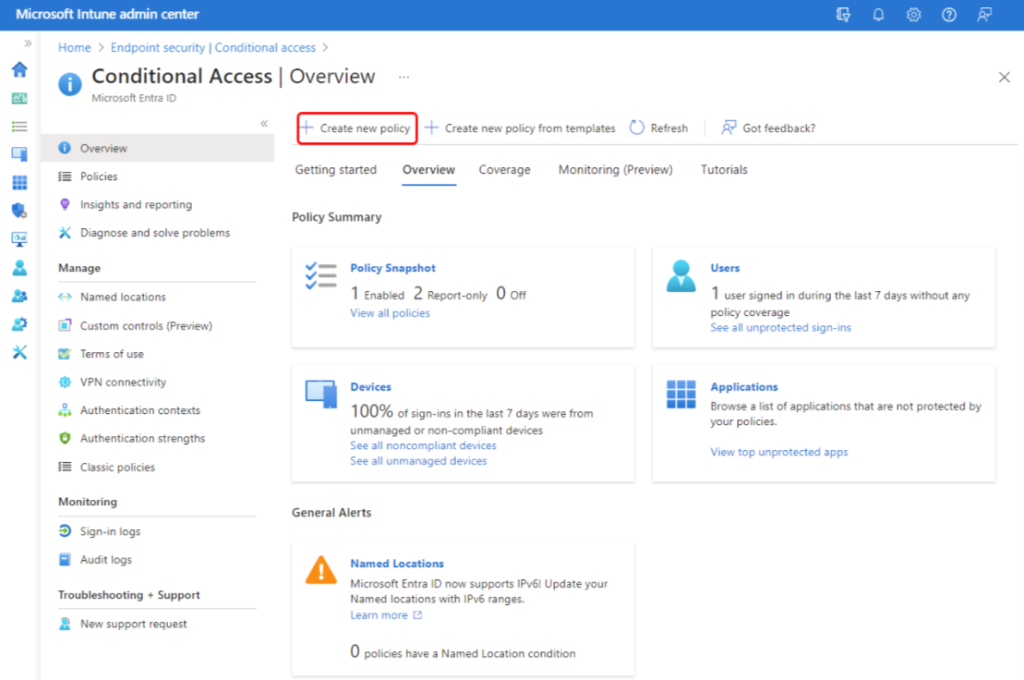
1. Sign in to Microsoft Intune Admin Center
Head to the Microsoft Intune admin center and navigate to:
Endpoint Security > Conditional Access > Create new policy.
This opens the New Policy pane — powered by Microsoft Entra — where you’ll define the rules for your Conditional Access setup.
2. Configure Assignments
Under Assignments, choose Users to define who the policy applies to.
- Include tab: Select users or groups that should be covered by the policy.
- Exclude tab: Exclude specific users or administrative roles that need broader access.
This ensures your policy targets only relevant personnel and avoids locking out essential accounts.
3. Set Target Resources
Next, configure Target resources under Assignments. From the dropdown menu, choose Cloud apps.
- Include tab: Select which apps or services you want to protect.
- Exclude tab: Exclude those that shouldn’t be affected.
This step determines exactly which digital assets your policy safeguards.
4. Define Conditions
Select Conditions to specify when this policy applies. You can base it on:
- User risk or sign-in risk (based on Azure AD signals)
- Device platforms (e.g., Windows, iOS, Android)
- Locations (e.g., trusted vs. untrusted IPs)
- Client apps (browser, mobile, or desktop)
- Device filters (to include or exclude certain configurations)
These criteria let you tailor security responses to specific situations — a best practice in modern cybersecurity.
5. Set Access Controls
Under Access controls, choose Grant to define how access is handled:
- Block access: Completely denies access under certain conditions.
- Grant access: Allows access but enforces additional requirements, such as:
- Requiring multi-factor authentication
- Using an approved client app
- Ensuring the device is marked as compliant
- Requiring a hybrid-joined device
Fine-tuning these controls ensures security without sacrificing usability.
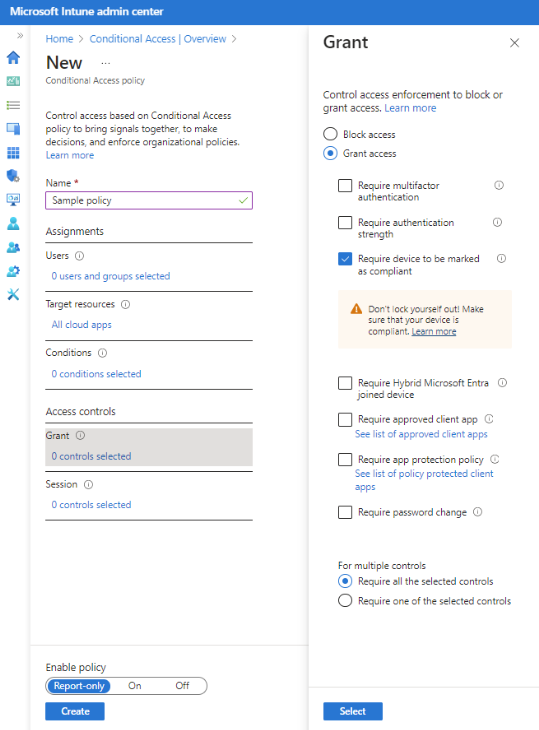
6. Enable and Deploy
Finally, under Enable policy, toggle it On (the default is Report-only). Then click Create to activate the policy.
Your Conditional Access configuration will now enforce secure sign-in behavior for the chosen users, apps, and conditions.
Why Work with an MSP in Canada for Conditional Access and Beyond
While these steps may seem straightforward, deploying Conditional Access at scale — across dozens of users, devices, and apps — requires careful planning and continuous monitoring. Misconfiguration can accidentally block critical access or leave security gaps.
Partnering with an experienced MSP in Canada like System Support Canada ensures your Conditional Access policies are properly designed, tested, and maintained. Here’s how our team adds value:
- 🔒 Advanced Cybersecurity Expertise: Our certified specialists continuously monitor, patch, and optimize your IT environment.
- 💾 Reliable Backup Services: Protect your Microsoft 365 data and servers with automated, encrypted backups and fast recovery options.
- 💬 24/7 IT Support and Helpdesk: Get real-time support whenever you need it — 365 days a year.
- 🌐 Full-Stack IT Solutions: From managed server and network maintenance to web design and SEO, we handle every part of your IT ecosystem.
- 💡 Tailored Business Continuity Plans: We align technology with your business goals, ensuring uptime, productivity, and compliance.
- 🤝 Transparent Pricing & Honest Service: No hidden fees. Just dependable, proactive support you can trust.
Conclusion: Protect Your Business with Expert IT Support in Toronto
Conditional Access is just one piece of a strong cybersecurity and access control strategy. By partnering with a trusted MSP in Canada like System Support Canada, you gain more than technical help — you gain a long-term technology partner committed to your success.
Whether you need backup services, managed server solutions, or 24/7 IT support in Toronto, our experienced team is ready to help your business stay secure, efficient, and future-ready.
Ready to strengthen your IT security and productivity?
Contact System Support Canada today for a free consultation or custom IT assessment.
📞 Call us: +1 (416) 987-1014
🌐 Visit: www.systemsupport.ca
📧 Email: [email protected]


